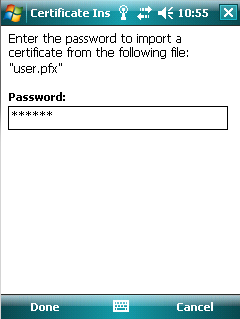
Install Exchange Certificate Windows Mobile 6.5
Windows Embedded Handheld (WEHH) 6.5 cannot connect to Office 365 Exchange Online through Exchange ActiveSync after certificate. Windows Mobile (WM) 6.5.
I have a HTC Touch Pro 2 with WM6.5 that does not keep the certificate for my exchange server. I install the certificate into the phone and setup the exchange settings in activesync, and it works fine for a while. After a day, activesync on the phone or desktop says certificate not valid.
Has anyone run into this type of issue? I have Windows Small Business Server 2008 with exchange, and a self signed certificate. My partner has NO PROBLEM with his HTC Fuze (WM6.1) and the same settings! Any information on this issue is greatly appreciated!!!
Thank you for your help. Is the certificate expired? Have you installed the certificate itself or the CA's certificate, the latter should be installed? Is the date on your computer and/or phone correct? A certificate will fail validation if a device's time is before issue date or after expiration date. Is your phone in Global mode instead of CDMA mode, I have seen issues where the phone's clock gets a weird date in Global mode. One can obtain a public CA signed UCC cert from GoDaddy for $90/yr that works out of the box.
Might be a better option if you have the budget for it. The proper way to self-sign a certificate is to install a Certificate Authority (CA) on your server. Then one generates a certificate request using Exchange and submits it to the Certificate Authority. The CA then signs the certificate with its private key and it is installed on the Exchange server. The CA's certificate (containing only its public key) is then installed on each client device. The device verifies the validity of the Exchange certificate utilizing the CA's certificate.
 Unfortunately, I am not sure what could be causing your problem.
Unfortunately, I am not sure what could be causing your problem.
• Supplies the necessary connection to a trusted root in an secure connection. • Must be installed on the server acting as a chain-link between the root (installed in the client) and the server certificate. • Does not control the encryption level.
This function is controlled by the server software. To install the RapidSSL Intermediate CA Certificate on Microsoft IIS 5, 6, 7 and 8 servers, as well as on Exchange 2003, 2007, 2010 and 2013 systems, preform the steps below on the server: Step 1: Download RapidSSL Intermediate CA Certificate 1. Select the Intermediate CA Certificate for your server certificate type. Copy and paste the contents of the Intermediate CA Certificate into Notepad. Save the file as intermediate.cer on your server. Step 2: Create a Certificate Snap-in 1.
From the Web server, click Start > Run 2. In the text box, type mmc 3. From the Microsoft Management Console (MMC) menu bar, select Console (in IIS 5) or File (in IIS 6, 7 and 8) > Add/Remove Snap-in 5. From the list of snap-ins, select Certificates 7. Select Computer account 9. Click Next 10.
Select Local computer (the computer this console is running on) 11. Click Finish 12. In the snap-in list window, click Close 13. In the Add/Remove Snap-in window, click OK 14. Save these console settings for future use. Step 3: Install the RapidSSL Intermediate CA certificate 1.
From the left pane, click Intermediate Certification Authorities 2. Right-click Certificates 3. Click All Tasks > Import 4. A Certificate Import Wizard, click Next 5.
Select the Intermediate CA Certificate file 6. Click Next 7.
Select Place all certificates in the following store: Intermediate Certification Authorities 8. Click Next 9. Click Finish 10. Restart the IIS services (iisreset). • • DigiCert is the world’s premier provider of high-assurance digital certificates—providing trusted SSL, private and managed PKI deployments, and device certificates for the emerging IoT market.
Since our founding almost fifteen years ago, we’ve been driven by the idea of finding a better way. A better way to provide authentication on the internet. A better way to tailor solutions to our customer’s needs. Now, we’ve added Symantec’s experience and talent to our legacy of innovation to find a better way to lead the industry forward, and build greater trust in identity and digital interactions.